35+ basic network diagram with firewall
The black hole information paradox is a puzzle that appears when the predictions of quantum mechanics and general relativity are combined. This Cisco ASA Tutorial gets back to the basics regarding Cisco ASA firewalls.

Network Diagram For Class Networking Diagram
Capture Point CPoint-FE0.
. We assume that our ISP has assigned us a static public IP address eg 2002002001 as an example and that our internal network range is 1921681024. O An originator generates syslog content to be carried in a message. GPS coordinates of the accommodation Latitude 43825N BANDOL T2 of 36 m2 for 3 people max in a villa with garden and swimming pool to be shared with the owners 5 mins from the coastal path.
Make sure port 59998 is open in Windows Firewall on each cluster node. The packet starts with a Basic Header of a single byte 0x03 where the two most significant bits b00000011 define a chunk header type of 0 while the rest b00000011 define a Chunk Stream ID of 3The four possible values of the header type and their significance are. Routing is the mechanism that allows a system to find the network path to another system.
There are three types of destinations. For conductive or fiber optical mediums this refers to the layout of cabling the locations of nodes and the links between the nodes and the cabling. Distributions include the Linux kernel and supporting system software and libraries many of.
Linux is typically packaged in a Linux distribution. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system. Rental price 70 per night.
Windows Firewall blocks health check. RFC 5424 The Syslog Protocol March 2009 Certain types of functions are performed at each conceptual layer. The physical topology of a network is determined.
Turla surveys a system upon check-in to discover active local network connections using the netstat -an net use net file and net session commands. Tropic Trooper has tested if the localhost network is available and other connection capability on an infected system using command scripts. Linux ˈ l iː n ʊ k s LEE-nuuks or ˈ l ɪ n ʊ k s LIN-uuks is a family of open-source Unix-like operating systems based on the Linux kernel an operating system kernel first released on September 17 1991 by Linus Torvalds.
We do insist that you abide by the rules and policies detailed below. The theory of general relativity predicts the existence of black holes that are regions of spacetime from which nothing not even light can escape. Learn how to configure your Cisco router to capture network packets through any interface using the Cisco IOS Embedded Packet Capture EPC.
Registration to this forum is free. Im offering you here a basic configuration tutorial for the Cisco ASA 5510 security appliance but the configuration applies also to the other ASA models as well see also this Cisco ASA 5505 Basic Configuration. B01 8 bytes - like type b00 not including message ID 4 last bytes.
Loop quantum gravity LQG is a theory of quantum gravity which aims to merge quantum mechanics and general relativity incorporating matter of the Standard Model into the framework established for the pure quantum gravity case. Associate member Area of expertise Affiliation. The route indicates that when trying to get to the specified destination send the packets through the specified gateway.
B00 12 byte header full header. The 5510 ASA device is the second model in the ASA series ASA 5505 5510. An intrusion detection system IDS.
See Open the Windows Firewall. Supervisory control and data acquisition SCADA is a control system architecture comprising computers networked data communications and graphical user interfaces for high-level supervision of machines and processes. If the health check isnt working double-check that you have a firewall rule to enable incoming traffic from the IP addresses that the health check system uses.
Without having to perform the detailed firewall setup as described in Section 234 firewalld you can determine the basic firewall configuration for your device as part of the device setup. O A collector gathers syslog content for further analysis. These are most commonly used to map human-friendly domain names to the numerical IP.
เวบไซตอนดบ 1 ของเมองไทยทรวม สารบญเวบ สารบญ. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. For example B may be receiving requests from many clients other than A andor forwarding.
RFC 2616 HTTP11 June 1999 may apply only to the connection with the nearest non-tunnel neighbor only to the end-points of the chain or to all connections along the chain. Examining the diagram below. A route is a defined pair of addresses which represent the destination and a gateway.
In the 1970s Stephen Hawking applied the rules of quantum mechanics to such. Individual hosts subnets and default. In this article I will explain the basic configuration steps needed to setup a Cisco 5505 ASA firewall for connecting a small network to the Internet.
Two basic categories of network topologies exist physical topologies and logical topologies. The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks. It also covers sensors and other devices such as programmable logic controllers which interface with process plant or machinery.
Although the diagram is linear each participant may be engaged in multiple simultaneous communications. Troubleshoot capture export examine and save packets from your router to tftp ftp http scp destination. The resource records contained in the DNS associate domain names with other forms of information.
O A relay forwards messages accepting messages from originators or other relays and sending them to collectors or other relays. Get 247 customer support help when you place a homework help service order with us. The transmission medium layout used to link devices is the physical topology of the network.
Medical population genomics Genetics Epidemiology Computational risk predication medical OMICS machine learning. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency. Linux Host Maximum Number of Open Files.
It is an attempt to develop a quantum theory of gravity based directly on Einsteins geometric formulation rather than the treatment of gravity. A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other. Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations.

Computer Network Architecture Computer And Network Examples Network Architecture Computer Network Diagram Architecture

Isometric Network Diagram By Bobby Hodges Diagram Design Visio Network Diagram Small Business Network

How Does A Firewall Protect A Network From Attacks
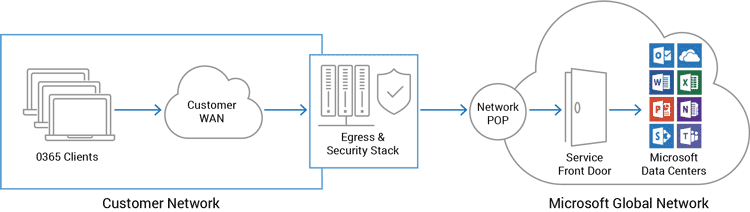
Microsoft Office 365 Enterprise Network Architecture A10 Networks

Network Address Translation Nat An Introduction Geekflare
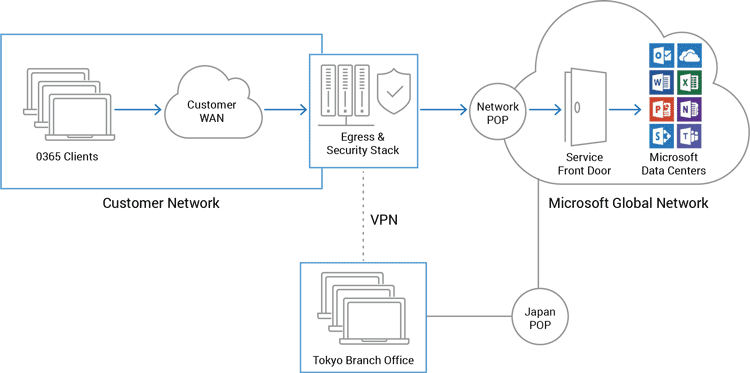
Microsoft Office 365 Enterprise Network Architecture A10 Networks
How Does A Firewall Protect A Network From Attacks

Zone Segmentation In A Office Network Local Network Security Diagram Design Diagram Segmentation
Help Me Build Most Secured Home Network To Last A Decade Techenclave Indian Technology Community

Pfsense Network Diagram Laptop Internet Xbox One Networking
Why Should I Buy A Physical Firewall When Wifi Routers Also Act As Firewalls Quora
2
Help Me Build Most Secured Home Network To Last A Decade Techenclave Indian Technology Community

What Is Firewall An Introduction Guide

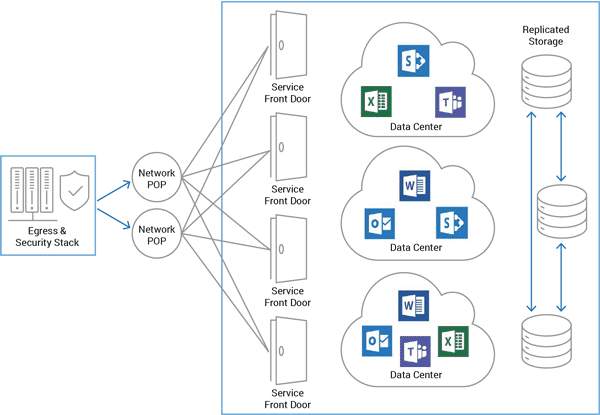
Microsoft Office 365 Enterprise Network Architecture A10 Networks

Computer Network Diagram Computer Network Pc Network Networking
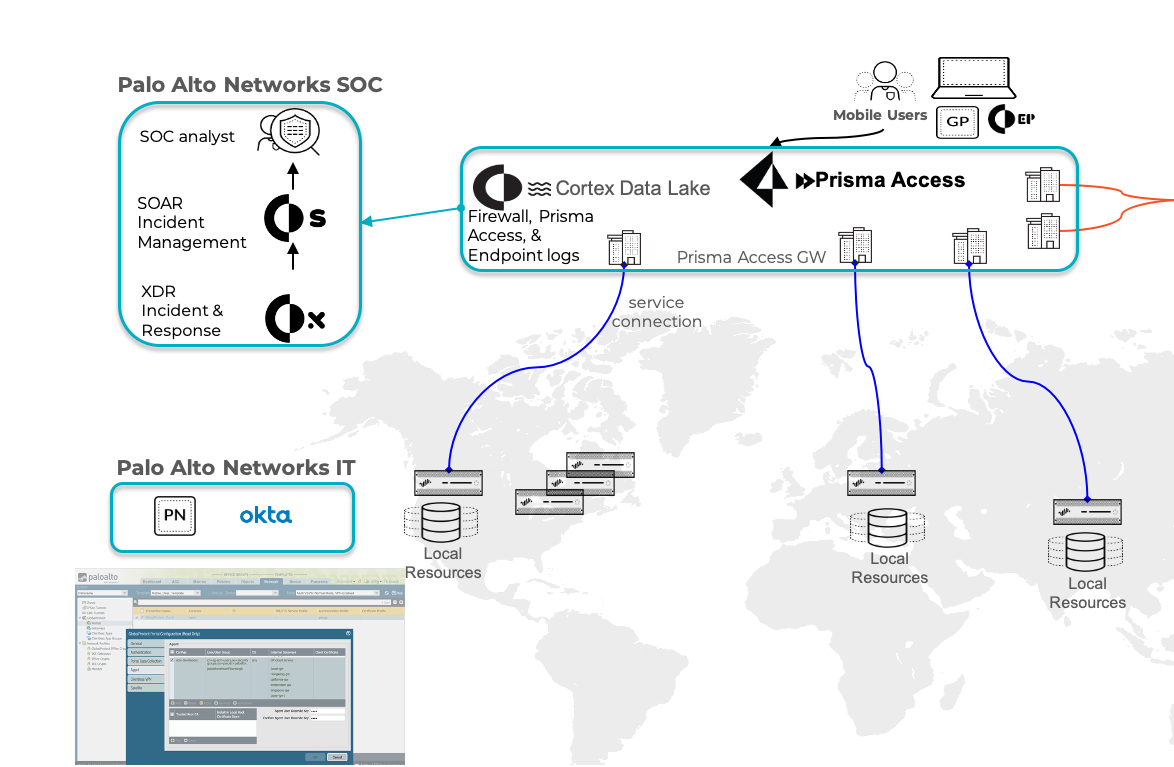
Securing Remote Workforce Worldwide With Prisma Access Tech Insider